Thursday, 5 November 2015
Thursday, 29 October 2015
Friday, 16 October 2015
Wednesday, 14 October 2015
Monday, 12 October 2015
ADVANCED FEATURES OF MS WORD
COURSE WORK
GRADE 6S
Write down the shortcut keys for the following functions:
- Apply Heading 1
- Apply Heading 2
- Apply Heading 3
- Apply list bullet
- Cancel
- Hanging Indent
- Copy format
- Normal style
- Paste format
- Thesaurus
Sunday, 11 October 2015
FETCH EXECUTE CYCLE ANIMATION TUTORIAL
The following link is a very user friendly and easy to learn tutorial on fetch execute cycle.
FETCH EXECUTE CYCLE ACTIVITY - CLASSWORK
Click on the link below to perform an activity on fetch execute cycle.
You will be graded on this activity. After completing the activity, take its print out and attach the sheet on your note books.
Saturday, 10 October 2015
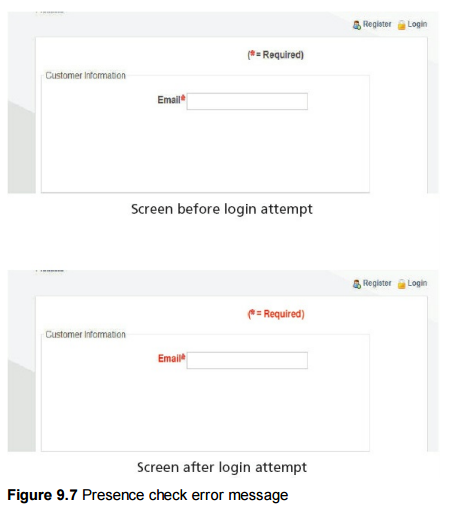
Validation
Validation is the automated checking by a program that data is reasonable before it is
accepted into a computer system. Different types of check may be used on the same
piece of data; for example an examination mark could be checked for reasonableness
by using a range check, a type check and a presence check. When data is validated by
a computer system, if the data is rejected a message should be output explaining why
the data was rejected and another opportunity given to enter the data.
Saturday, 3 October 2015
Wednesday, 30 September 2015
LOSSY AND LOSSLESS COMPRESSION
Show understanding of the principles of data compression (lossless and lossy compression algorithms) applied to music/video, photos and text files
When data other than text is being transmitted, e.g. on the Internet, it is important to limit the amount of data that needs to be sent to stop the time taken to download the data being unreasonably long. The amount of data can be limited by reducing the file size of pictures so that they take up only a small part of the screen or restricting them to a few colours. Speeding up the transmission of the data is achieved by reducing the amount of data that is sent. This is known as file compression.
Compression can be either lossy or lossless. Lossless compression means that no data is lost.
LOSSY COMPRESSION
Lossy compression involved sacrificing some of the data in order to reduce the file size. Lossy compression techniques reduce the quantity of data in two ways. First by using complex mathematical encoding and secondly by deliberately losing some types of visual information that our eyes and brain usually ignore (this is called quantization).
For example, the video frame rate may be reduced from the normal 25 frames per second down to around 15 frames per second before there is a perceptible loss in quality. The frames themselves may be treated as separate still images, and compressed individually using JPEG compression. Different areas of a frame may be compressed by different degrees – an area of blue sky which lacks detail might be compressed by 25:1, whereas a person’s face might only be compressed by 5:1. Depending on the amount of action in the video, only some areas of each frame may change from one frame to the next and only the changed data need be stored. The size of the picture may also be reduced, reducing the overall quantity of pixels to be stored.
If lossy compression is taken to an extreme, it can result in a significant loss of picture quality. The higher the compression ratio, the worse the resulting image. For instance, colour fidelity fades and the edges of objects become very obvious, until eventually the results is unwatchable.
JPEG image compression works in part by rounding off nonessential bits of information. There is a corresponding trade-off between preserving information and reducing size. A number of popular compression formats exploit these perceptual differences, including those used in music files, images, and video. Lossy image compression can be used in digital cameras, to increase storage capacities with minimal degradation of picture quality. Similarly, DVDs use the lossy MPEG-2 Video codec for video compression.
LOSSLESS COMPRESSION
Lossless compression uses mathematical techniques such as Huffman coding or Discrete Cosine Transformation (DCT), to reduce the quantity of information to be stored, while still being capable of reproducing the original image without any loss in quality.
Lossless data compression algorithms usually exploit statistical redundancy to represent data more concisely without losing information, so that the process is reversible. Lossless compression is possible because most real-world data has statistical redundancy. For example, an image may have areas of colour that do not change over several pixels; instead of coding "red pixel, red pixel, ..." the data may be encoded as "279 red pixels". This is a basic example of run-length encoding; there are many schemes to reduce file size by eliminating redundancy.
Compression standards include MPEG, M-JPEG, Cinepak,
ONLINE COLLABORATION - COURSEWORK
ONLINE COLLABORATION - COURSEWORK
Q 1: Differentiate between audio and
video conferencing. [2]
Q 2: Enlist items required for a video
conferencing. [2]
Q 3: Explain the advantages and
disadvantages of video conferencing. [2]
Q 4: Disadvantages of social
networking. [2]
Q 5: Explain the usage of Skype. [2]
Monday, 28 September 2015
Sunday, 27 September 2015
GRADE 9 ASSIGNMENT (Deadline Monday, 5th October'15)
MEMORY AND STORAGE DEVICES:
- The below mentioned assignment must be submitted on 5th October'15.
- In case of late submission, 2 marks will be deducted.
- Assignment must be NEATLY done on your notebooks. (don't forget to write the complete questions )
ANSWER THE FOLLOWING QUESTIONS:
- Describe 2 difference between RAM and ROM.
- Describe what is stored on RAM and ROM , also explain why that type of memory is appropriate.
- State one type of software which must be stored in a computer’s ROM, justifying your answer.
- Name three different types of storage media and give an example of each.
- State one type of software which must be stored in a computer’s RAM, justifying your answer.
Saturday, 5 September 2015
Gas Sensor
A gas sensor produces a signal that depending on the concentration of a particular gas or vapour. We can use a sensor for an inflammable gas to monitor the atmosphere and sound an alarm if there is a leakage of, for example, liquid propane gas that could cause an explosion.
Gas sensor can also be used in the following applications:
- environmental monitoring of air pollution.
- process control in the chemical industry.
Humidity Sensors
A humidity sensor produces a signal that depends on the concentration of water vapour in the atmosphere. A similar device for use in soil is called a moisture sensor.
If an irrigation system is controlled by a clock, the soil is watered at set times even when it is already moist enough. A moisture sensor can control an irrigation system more efficiently. A sensor-enabled 'smart' irrigation controller only waters when the soil is dry.
Thursday, 3 September 2015
Sunday, 30 August 2015
Thursday, 27 August 2015
Saturday, 10 January 2015
ICT - Algorithms (Selection & Iteration)
Algorithms
An algorithm is a plan, it is a set of step-by-step instructions to solve a particular problem. There are three basic building blocks or constructs to use when designing an algorithm:
They are as under:
- sequencing
- selection
- iteration
Sequencing
Sequencing is a process that provides a solution to your problem in number of steps in a particular sequence.
Selection
Example for selection process includes : How old are you?
An algorithm consists of a set of instructions that are carried out one after an another. Sometimes in any situation, there may be more than one path or steps that can be followed. At that point, a particular decision needs to be made. This point is known as selection.
For example, The following algorithm can be created to determine correct bus charges.
Following are the steps:
Following are the steps:
- first of all, ask how old you are ?
- if your age is under 13, then pay half charges
- otherwise just pay full charges.
The decision comes in step number 2. If you are aged, that is less than 13, only one fare is charged. Otherwise, a different fare is being charged.
IF ...THEN...ELSE
A selection process allows several paths to be included in an algorithm. In algorithms, a selection is usually represented by the instructions that is IF, THEN and ELSE.
- IF - It represents the question
- THEN - It points to what to do (or choose option) if the answer to the desired question is true
- ELSE - It points to what to do(or what to choose) if the answer to the desired question is false
Using this method, the fare-related algorithm that we had discussed before now reads like this:
ask how old you are
IF you are under 13, THEN pay half fare
ELSE pay full fare
If you try the above algorithm using 12 as your age, then the answer to the question at step number 2 will be absolutely true, so the algorithm tells us that we will pay only half fare.
But if suppose we try the above algorithm using 13 as our age, the answer to the question at step number 2 will be false, so the algorithm tells us that we have to pay full fare.
Hence, two different paths are followed according to the answer given to a particular question.
DOWNLOAD
DOWNLOAD
Subscribe to:
Comments (Atom)